**This is part of our series highlighting startups who share our mission of trying to make people’s lives just a little easier**
The explosion of new technologies has seen a huge rise in the quantity and – more importantly – the quality of cyber hackers out there. Crude attempts to hack into systems are a thing of the past, and instead expert attackers are collaborating with governments and crime syndicates to do questionable things with data.
For digital businesses in particular, this is a big concern. Large, distributed networks that are scattered around the web lend themselves perfectly to cyber-attacks from sophisticated hackers, and those hackers are more savvy than ever before.
New Israel-based startup Illusive Networks was built to stop these attackers in their tracks – literally (albeit digitally).

Malicious hackers will find every entry point they can to wriggle into a network, often bypassing firewalls that companies thought would protect them and their assets. Because of this, Illusive Networks has said goodbye to firewalls and has instead gone for a different method of creating a new world for the hacker to disappear into (and get lost).
If it sounds like something out of Minority Report, you might be onto something. And, if it sounds a bit farfetched, you’re on the same wavelength as us. I mean, creating a whole new world simply to distract potential hackers seems like a lot of extra effort, right?
This is where it gets interesting.
You’ve heard of virtual and augmented reality, right? These are two new technologies that layer an alternate reality over the top of, well, real reality to bring participants new perspectives and new worlds entirely.
Illusive Networks taps into these technologies and creates a false version of a company’s network to either trap the hackers in an alternate “reality” or kick them out completely.
Isn’t Illusive Networks Just Like the Others?
The answer to this question is, of course, yes and no.
Businesses have access to thousands of different security products these days, and there seems to be a new anti-cyberattack startup popping up every single day.
Because of this, business owners and security leaders are resisting adding even more tools to their security arsenal – the last thing people want or need are noisy alerts every time a hacker tries to break through a digital barrier.
“But technologies that truly look at existing problems in new ways and are purpose-built to help companies deal with the unexpected can deliver significant efficiencies that reduce rather than add to the security burden,” says Illusive Networks’ Founder and CEO, Ofer Israeli. “Distributed deception technology is certainly one of them.”
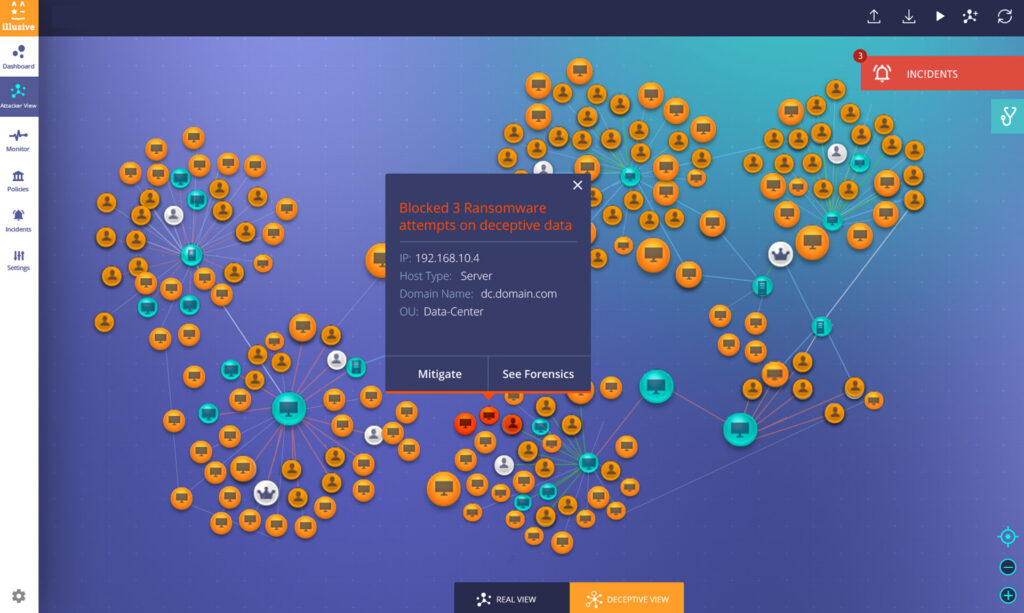
How Illusive Networks Works
On its website, Illusive Networks says that it:
- Maps potential paths attackers can take to get to the goods (a.k.a. your most important assets)
- Finds and gets rid of risky areas that help attackers reach your assets
- Cloaks your system with thousands of high-fidelity deceptions that trigger an alert when one wrong move is detected
- Offers real-time forensic reports to help response teams stay in control
But what do all these things really mean? And what even is “distributed deception technology”?

“There will always be a phishing or drive-by attack,” says Israeli. “Humans are the weakest link and always will be and will continue to make mistakes. But once the hacker is in, now we have an attacker who needs to orient himself.”
Essentially, distributed deception means creating a series of fake journeys a potential hacker could take. The aim is to confuse, deceive, and catch them red handed.
Illusive Networks creates an “illusive” version of a company’s network (that alternate reality we were talking about earlier). And, once a hacker finds themselves in this parallel universe, the tool identifies the individual and either keeps them shut in there forever or kicks them out for good.

Think about it: to strategically plan a pathway to the main asset, a hacker needs to consider two things. They need to know what options they have for where they can go next, and they need to know how they can access the powers needed to execute that particular move. In the security world, this two-step process is known as orientation and propagation.
You see, to get to the coveted prize, a hacker needs to make a series of hundreds or thousands of tiny moves – something that Illusive Network aims to put a rapid stop to.
Say, for example, there’s a hacker who has the option to take three different paths towards their next step. Illusive Networks then swoops in with a further twenty choices, of which only three are real and the other seventeen are traps. If the hacker takes any of those seventeen options which, let’s face it, is highly likely with the law of probability, the system is alerted to an unwanted intruder.
Likewise, if a hacker needs to gain credentials to make their next move, Illusive Networks will supply them with tens more credentials than they need so that, again, if they pick the wrong choice the system goes into lockdown.
So, rather than shutting out hackers entirely like firewalls do, Illusive Networks deceives them so it’s almost impossible for them to reach their end goal. The startup has even brought several ex-attackers on board who have shared their perspectives to make solutions more realistic and useful.
Perhaps the most advanced thing about the startup is that neither the professionals working for Illusive Networks nor the hackers can see the deceptions until they walk into them head first. This means the deception sensors are only triggered if someone “bumps into them”, but it also means that it only takes a few moves (out of potentially thousands) for an attacker to be detected and kicked out.
What Does This Mean for the Future of Cyber Attacks and Data Breaches?
Illusive Networks plans to bring a new age of security to digital businesses that will see less hackers succeeding despite them getting more and more sophisticated every day.
Data breaches could be a thing of the past, as distributed deception means hackers don’t have to just navigate one obstacle like a firewall. Instead, there are obstacles all around them (think security lasers in a museum as a real-life example), and every wrong move can be quickly detected.
But while it might be comforting to know that our personal data looks to be safer than ever, the technology behind Illusive Networks might not be limited stopping hackers in the future.
What if hackers start using it to their advantage? These are people that are highly skilled in tech-endeavors, so surely they’re buffing up on this new technology as we speak and working out ways they can use it to their benefit? If they’re not, maybe they’re missing a trick.
Systems like the one Illusive Networks is using are groundbreaking in the war against cyber attacks but only time will tell if they’re victorious.


