With data breaches happening more frequently than we’ve ever seen, data privacy has truly become a hot-button issue. It seems like every week, a new story is trending about how a corporation compromised the data privacy of its customers. It’s very evident that mainstream methods of storing data are leaving everyone vulnerable. They’re simply not enough to protect the data privacy of customers or put an end to those damaging data breaches once and for all. However, moving to a blockchain-based method of storing data could yield great returns in maintaining data privacy for both giant corporations and individuals. It could put an end to our data privacy being compromised.
If you spend much time on the internet, it’s inevitable that you’ll run into the term “blockchain” eventually. It’s usually mentioned in connection with cryptocurrencies like Bitcoin or Ethereum, which pride themselves on anonymity. However, the ability of blockchain to provide protection and data privacy goes far beyond financial security and cryptocurrencies. If leveraged in a way that harnesses its greatest strengths, blockchain technology could make it much harder for hackers and others to breach networks and gain access to private information. It could be the official “goodbye” to data breaches and the “hello” to full data custody.
What Causes Data Breaches?
Companies that work with sensitive information typically keep records of this info. Items such as credit card numbers, social security numbers, medical history and more are stored by everyone from hospitals to Amazon to your local grocery store. When it comes to storing information today, there’s one mainstream method: centralized storage.
In the early days of the internet, the speed at which computers could communicate was slow. For companies to work with significant amounts of information, it was mandatory that it be somewhere local. Many companies had their own server banks that stored only their information. These servers were frequently connected to the local network and nothing else. Having to interact with information on the internet was too slow to be useful for everyday business.
As the internet grew, however, two things began to change. First, internet speeds increased. Whereas it used to take hours to download a short video, many people now have the speed to stream movies in high-definition instantly. Second, hosting companies began to emerge. These companies run server banks and take on the cost of the hardware, maintenance, and electricity that storing a lot of information required. With quicker internet and the option to cut their own expenses, most companies outsourced their data hosting. Instead of a bunch of decentralized, disconnected servers, there are a few centralized, highly-connected server farms.
Unfortunately, this new arrangement provides another perfect environment to foster data breaches. Before, getting into a small company’s servers was a lot of work for little payoff. They may not even be accessible through the internet, depending on the business. However, a big server farm that hosts websites for some and databases for others needs to be connected to the web. Getting into the system may be difficult, but the payoff could be the credit card info for thousands or even millions of people. Many hackers think that the time spent is worth the results.
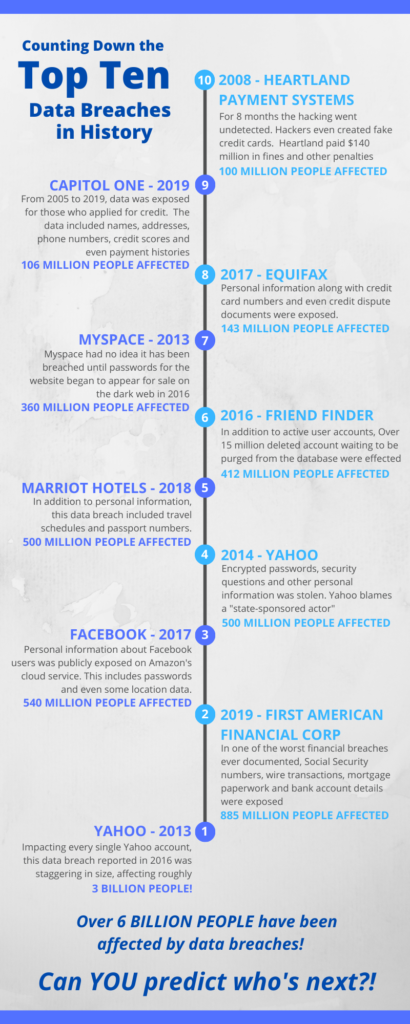
The Equifax breach is a good example of a modern data breach. Equifax maintains records of the financial information of most US citizens. Hackers got access to servers containing 148 million people’s social security numbers by slipping through inadequate security on Equifax’s online complaint portal. Because of security flaws, that portal was connected to other, more important servers. If Equifax did not have such centralized systems, or if they had updated their security, this breach would not have been possible.
Blockchain: Data Privacy without Trust
Because most security systems require things like updates, renewed certifications, and passwords, they are subject to a lot of human error. The Equifax breach occurred in part because people stored passwords in plain text and a single encryption key wasn’t updated. By removing the option for human error from the equation, information becomes much more secure.
That’s where decentralized networking comes in. In decentralized networks, the control of the network is distributed between the nodes (or servers running the blockchain and the network) as opposed to being collocated within the same server center (centralized). This makes it much harder for hackers and others to breach the network. As an example, if a hacker were to pursue breaching Equifax, they would know to start with Equifax. But to breach a blockchain network that is both decentralized and distributed is a much larger task, with no way of knowing what the potential payoff would be.
Blockchain networks share the blockchain itself (a public ledger) between each node on the blockchain network. Every node has a copy of the entire blockchain. This means that every node can be sure that every other node has the right chain information because they are all identical. This is where the trust between nodes in a decentralized network comes into play. In order for a blockchain to be corrupted, a hacker would need to take control of the majority of the nodes in the network. Specifically, the hacker would need to control 51% of these nodes (https://www.investopedia.com/terms/1/51-attack.asp) in order to make any changes to the blockchain. Naturally, this is a significant undertaking for any hacker to pursue, especially since they have no way of knowing what their rewards would potentially be as they wouldn’t know what is being managed through the blockchain.
Managing personal data such as files through a decentralized and distributed network also offers security advantages over centralized solutions. The Interplanetary File System (IPFS) is one way this can be done. Essentially, every file or document would be given its own cryptographic hash. The files are stored somewhere on the decentralized network, and in order to get them out, you must know their exact hash. Without that info, you can never get to the file. That allows for servers around the world to hold information without anyone being able to access the information fraudulently. Instead of relying on centralized server farms and their security, blockchain and IPFS allow for people to host things on small, decentralized servers without worrying.
Where Equifax had its complaints portal running on a centralized server, blockchain would make that unnecessary. Through decentralized apps (dAPPs), everything from websites to games to entire banking systems could be run through decentralized networks. This is the Internet 3.0. It’s the next stage of the web’s evolution. So far, we’ve come from tiny, poorly connected sites (Internet 1.0) to big, centralized sites (Internet 2.0). We can make it to the next step: big, useful, decentralized sites, apps, financial systems, and more.
Blockchain vs. Breaches: A Clear Winner
A big data breach is only possible if many people’s information is stored in one place. Blockchain and decentralization not only make breaches difficult, they make centralization irrelevant. There’s no need to store many things in one central place when you can store it on a network with complete confidence in your privacy. The blockchain process is the next step in the evolution of the internet. From finances to healthcare to social media, blockchain and decentralization will help us all maintain ownership over our own data, no breaches allowed.